I’m at IMC 2017 at Queen Mary University of London, and will try to liveblog a number of the sessions that are relevant to security in followups to this post.
Category Archives: Spam
Phishing that looks like another risk altogether
I came across an unusual DHL branded phish recently…
The user receives an email with the Subject of “DHL delivery to [ xxx ]June ©2015” where xxx is their valid email address. The From is forged as “DHLexpress<noreply@delivery.net>” (the criminal will have used this domain since delivery.net hasn’t yet adopted DMARC whereas dhl.com has a p=reject policy which would have prevented this type of forgery altogether).
The email looks like this (I’ve blacked out the valid email address):
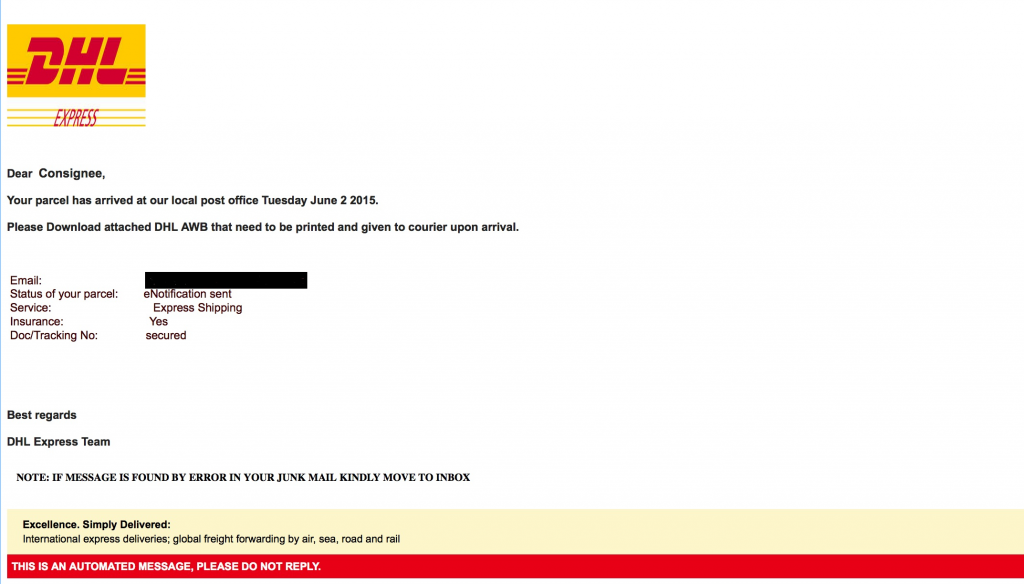
and so, although we would all wish otherwise, it is predictable that many recipients will have opened the attachment.
BTW: if the image looks in the least bit fuzzy in your browser then click on the image to see the full-size PNG file and appreciate how realistic the email looks.
I expect many now expect me to explain about some complex 0-day within the PDF that infects the machine with malware, because after all, that’s the main risk from opening unexpected attachments isn’t it ?
But no!
Continue reading Phishing that looks like another risk altogether
We're hiring again
We have a vacancy for a postdoc to work on the economics of cybercrime for two years from January. It might suit someone with a PhD in economics or criminology and an interest in online crime; or a PhD in computer science with an interest in security and economics.
Security economics has grown rapidly in the last decade; security in global systems is usually an equilibrium that emerges from the selfish actions of many independent actors, and security failures often follow from perverse incentives. To understand better what works and what doesn’t, we need both theoretical models and empirical data. We have access to various large-scale sources of data relating to cybercrime – email spam, malware samples, DNS traffic, phishing URL feeds – and some or all of this data could be used in this research. We’re very open-minded about what work might be done on this project; possible topics include victim analysis, malware analysis, spam data mining, data visualisation, measuring attacks, how security scales (or fails to), and how cybercrime data could be shared better.
This is an international project involving colleagues at CMU, SMU and the NCFTA.
Debunking cybercrime myths
Our paper Measuring the Cost of Cybercrime sets out to debunk the scaremongering around online crime that governments and defence contractors are using to justify everything from increased surveillance to preparations for cyberwar. It will appear at the Workshop on the Economics of Information Security later this month. There’s also some press coverage.
Last year the Cabinet Office published a report by Detica claiming that cybercrime cost the UK £27bn a year. This was greeted with derision, whereupon the Ministry of Defence’s chief scientific adviser, Mark Welland, asked us whether we could come up with some more defensible numbers.
We assembled a team of experts and collated what’s known. We came up with a number of interesting conclusions. For example, we compared the direct costs of cybercrimes (the amount stolen) with the indirect costs (costs in anticipation, such as countermeasures, and costs in consequence such as paying compensation). With traditional crimes that are now classed as “cyber” as they’re done online, such as welfare fraud, the indirect costs are much less than the direct ones; while for “pure”cybercrimes that didn’t exist before (such as fake antivirus software) the indirect costs are much greater. As a striking example, the botnet behind a third of the spam in 2010 earned its owner about $2.7m while the worldwide costs of fighting spam were around $1bn.
Some of the reasons for this are already well-known; traditional crimes tend to be local, while the more modern cybercrimes tend to be global and have strong externalities. As for what should be done, our research suggests we should perhaps spend less on technical countermeasures and more on locking up the bad guys. Rather than giving most of its cybersecurity budget to GCHQ, the government should improve the police’s cybercrime and forensics capabilities, and back this up with stronger consumer protection.
Beware of cybercrime data memes
Last year when I wrote a paper about mitigating malware I needed some figures on the percent of machines infected with malware. There are a range of figures, mainly below 10%, but one of the highest was 25%.
I looked into why this occurred and wrote it up in footnote #9 (yes, it’s a paper with a lot of footnotes!). My explanation was:
The 2008 OECD report on Malware [14] contained the sentence “Furthermore, it is estimated that 59 million users in the US have spyware or other types of malware on their computers.” News outlets picked up on this, e.g. The Sydney Morning Herald [20] who divided the 59 million figure into the US population, and then concluded that around a quarter of US computers were infected (assuming that each person owned one computer). The OECD published a correction in the online copy of the report a few days later. They were actually quoting PEW Internet research on adware/spyware (which is a subtly different threat) from 2005 (which was a while earlier than 2008). The sentence should have read “After hearing descriptions of ‘spyware’ and ‘adware’, 43% of internet users, or about 59 million American adults, say they have had one of these programs on their home computer.” Of such errors in understanding the meaning of data is misinformation made.
We may be about to have a similar thing happen with Facebook account compromises.
Continue reading Beware of cybercrime data memes
Complaining about spam to the ICO
Like I imagine most readers of Light Blue Touchpaper, the vast majority of spam I receive is from overseas. For that you can try complaining to the sender’s ISP, but if the spam is being sent from a botnet, there’s not much you can do to stop them sending you more in the future. There might be an unsubscribe link, but clicking on it will just tell the sender that your address has a real person behind it, and might encourage them to send more spam.
Things are different if the sender (of spam email or text messaging) is in the UK, because then they might have violated the Privacy and Electronic Communications Regulations (PECR), and you can complain to the Information Commissioner’s Office (ICO). The process isn’t fast, or particularly easy, and there are plenty of ways the ICO can avoid investigating, but it can get results.
The last time I went through this process was regarding a PR agency which was sending me repeated emails despite me asking to unsubscribe. I sent the complaint to the ICO in November 2010, and it took over 2 months for them to deal with it, but the ICO did conclude that based on the information available, the PR agency did violate the PECR. At the time, the ICO didn’t have powers to punish an organisation for PECR violations but they did remind the agency of their obligations. I was finally unsubscribed from the list and the PR agency even sent me a box of muffins as an apology.
Things don’t always go smoothly though. Before then I complained about an online DVD rentals company, for similar reasons. The ICO initially refused to invoke the PECR, claiming that “If you work for or attend higher education and are receiving unsolicited marketing emails to a university email address, there is no enforceable opt-out right provided by The Privacy and Electronic Communications Regulations 2003 (the Regulations).” However, they did say that if my name is identifiable from my email address, then the sender is processing personal data and thus is covered by the Data Protection Act. I could therefore ask the company to unsubscribe me (which I had done), and if they continued to send me email after 28 days I could complain to the ICO again.
In fact, the email address to which I was sent the spam was my personal address (I did however send the complaint from my university address), which I told the ICO. The ICO then wrote to the company reminding them of their obligations. I never received further emails from the company so it probably worked, but I didn’t get any muffins or even an apology from them.
Since then, some things have changed — particularly that the ICO can now fine organisations up to £500,000 for very serious breaches of the PECR (although as far as I can tell the ICO has never done so). Hopefully this will encourage organisations to take their obligations seriously. I’ve sent a further complaint to the ICO, so I’ll keep you posted on how this progresses. If you want to try sending a complaint yourselves, instructions can be found on the ICO site.