TL;DR
Two invitations to Cambridge (UK):
2025-03-25: the Rossfest Symposium, in honour of Ross Anderson (1956-2024)
https://www.cl.cam.ac.uk/events/rossfest/
2025-03-26 and 27: the 29th Security Protocols Workshop
https://www.cl.cam.ac.uk/events/spw/2025/
Start writing, and sign up here for updates on either or both:
https://forms.gle/Em9Hy43aRqrdGmd17
Rossfest Symposium
25 March 2025
The Rossfest Symposium and its posthumous Festschrift is a celebration and remembrance of our friend and colleague Ross Anderson, who passed away suddenly on 28 March 2024, aged 67.
Ross Anderson FRS FRSE FREng was Professor of Security Engineering at the University of Cambridge and lately also at the University of Edinburgh. He was a world-leading figure in security. He had a gift for pulling together the relevant key people and opening up a new subfield of security research by convening a workshop on the topic that would then go on to become an established series, from Fast Software Encryption to Information Hiding, Scrambling for Safety, Workshop on Economics and Information Security, Security and Human Behavior and so forth. He co-authored around 300 papers. His encyclopedic Security Engineering textbook (well over 1000 pages) is dense with both war stories and references to research papers. An inspiring and encouraging supervisor, Ross graduated around thirty PhD students. And as a contagiously enthusiastic public speaker he inspired thousands of researchers around the world.
The Rossfest Symposium is an opportunity for all of us who were touched by Ross to get together and celebrate his legacy.
The Festschrift volume
Scientific papers
We solicit scientific contributions to a posthumous Festschrift volume, in the form of short, punchy papers on any security-related topic. These submissions will undergo a lightweight review process by a Program Committee composed of former PhD students of Ross:
- Joseph Bonneau, New York University
- Richard Clayton, University of Cambridge
- Markus Kuhn, University of Cambridge
- Tyler Moore, University of Tulsa
- Ilia Shumailov, Google DeepMind
- Frank Stajano, University of Cambridge
Accepted papers will be published in the Festschrift book and presented at the event. For a subset of the accepted papers, the authors will be invited to submit an expanded version to a special issue of the Journal of Cybersecurity honouring Ross’s scholarly contributions and legacy.
Submissions are limited to five pages in LNCS format (we did say short and punchy!) and will get an equally short presentation slot at the Rossfest. Let’s keep it snappy, as Ross himself would have liked. Five pages excluding bibliography and any appendices, that is, and maximum eight pages total.
Topic-wise, anything related to security, taking the word in its broadest sense, is fair game, from cryptography and systems to economics, psychology, policy and much more, spanning the wide spectrum of fields that Ross himself explored over the course of his career. But make it a scientific contribution rather than just an opinion piece.
Authors will grant us a licence to publish and distribute their articles in the Festschrift but will retain copyright and will be able to put their articles on their web pages or resubmit them wherever else they like. We won’t ask for article charges for publishing in the Festschrift. Bound copies of the Festschrift volume will be available to purchase at cost during the Rossfest Symposium, or later through print-on-demand. A DRM-free PDF will be available online at no charge.
Informal memories
We also solicit informal “cherished memories” contributions along the lines of those collected by Ahn Vu at anderson.love. These too will be collected in the volume and a selection of them will be presented orally at the event.
The Rossfest Symposium
The Rossfest Symposium will last the whole day and will take place at the Computer Laboratory (a.k.a. the Department of Computer Science and Technology of the University of Cambridge), where Ross taught, researched and originally obtained his own PhD. Street address: 15 JJ Thomson Avenue, Cambridge CB3 0FD, UK.
Attendance at the Rossfest Symposium is free and not conditional on the submission of a contribution, but registration will be required for us to manage numbers and catering.
In the evening there shall also be a formal celebration banquet at Trinity College. To attend, please purchase a ticket. Registration and payment links shall appear on this page in due course. Street address: Trinity Street, Cambridge CB2 1TQ, UK.
We have timed the Rossfest to be adjacent in time and space to the Security Protocols Workshop, an event that Ross regularly attended. The SPW will take place in Trinity College Cambridge on 26 and 27 March 2025. This will allow you to attend both events with a single trip to Cambridge. Note that attendance at SPW requires presenting a position paper: unlike the Rossfest, at SPW all attendees must also speak.
Accommodation in Cambridge
The chosen dates are out of term, meaning you might be able to book a room in one of the 31 colleges through www.universityrooms.com. Otherwise, consider www.airbnb.com, www.booking.com, www.expedia.com or your favourite online booking aggregator.
Sign up
To receive notifications (e.g. “the registration and payment links are now up”), sign up on this Google form. Self-service unsubscribe at any time.
Dates
25 November 2024: Deadline for submission of Festschrift articles
23 December 2024: Invitations to authors to present orally
13 January 2025: Early bird (discounted) registration deadline for banquet
10 February 2025: Final registration deadline for banquet and symposium
25 March 2025: Rossfest Symposium (and optional banquet)
26-27 March 2025: Security Protocols Workshop (unrelated but possibly of interest)
Security Protocols Workshop
26 and 27 March 2025
The Twenty-ninth International Workshop on Security Protocols will take place from Wednesday 26 March to Thursday 27 March 2025 in Cambridge, United Kingdom. It will be dedicated to the memory of Ross Anderson and preceded by the Rossfest Symposium, which will take place on Tuesday 25 March 2025, also in Cambridge, UK. Come to both!
As in previous years, attendance at the International Workshop on Security Protocols is by invitation only. (How do I get invited? Submit a position paper.)
Theme
The theme of the 2025 workshop is: “Controversial Security – In honour of Ross Anderson”. In other words, “any security topic that Ross Anderson might have wanted to debate with you”, which leaves you with plenty of leeway.
This is a workshop for discussion of novel ideas, rather than a conference for finished work. We seek papers that are likely to stimulate an interesting discussion. New authors are encouraged to browse through past volumes of post-proceedings (search for Security Protocols Workshop in the Springer LNCS series) to get a flavour for the variety and diversity of topics that have been accepted in past years, as well as the lively discussion that has accompanied them.
Details
The long-running Security Protocols Workshop has hosted lively debates with many security luminaries (the late Robert Morris, chief scientist at the NSA and well known for his pioneering work on Unix passwords, used to be a regular) and continues to provide a formative event for young researchers. The post-proceedings, published in LNCS, contain not only the refereed papers but the curated transcripts of the ensuing discussions (see the website for pointers to past volumes).
Attendance is by invitation only. To be considered for invitation you must submit a position paper: it will not be possible to come along as just a member of the audience. Start writing now! “Writing the paper is how you develop the idea in the first place”, in the wise words of Simon Peyton-Jones.
The Security Protocols Workshop is, and has always been, highly interactive. We actively encourage participants to interrupt and challenge the speaker. The presented position papers will be revised and enhanced before publication as a consequence of such debates. We believe the interactive debates during the presentations, and the spontaneous technical discussions during breaks, meals and the formal dinner, are part of the DNA of our workshop. We encourage you to present stimulating and disruptive ideas that are still at an initial stage, rather than “done and dusted” completed papers of the kind that a top-tier conference would expect. We are interested in eliciting interesting discussion rather than collecting archival material.
Submissions
Short indicative submissions are preferred. You will have the opportunity to extend and revise your paper both before the pre-proceedings are issued, and again after the workshop. At the workshop, you will be expected to spend a few minutes introducing the idea of your paper, in a way that facilitates a longer more general discussion. Pre-proceedings will be provided at the workshop. See the Submission page for more details.
Committee
• Fabio Massacci (Program Chair), University of Trento / Vrije Universiteit Amsterdam
• Frank Stajano (General Chair), University of Cambridge
• Vashek (Vaclav) Matyas, Masaryk University
• Jonathan Anderson, Memorial University
• Mark Lomas, Capgemini
Accommodation in Cambridge
The chosen dates are out of term, meaning you might be able to book a room in one of the 31 colleges through www.universityrooms.com. Otherwise, consider www.airbnb.com, www.booking.com, www.expedia.com or your favourite online booking aggregator.
Dates
25 November 2024: Submission of position papers
23 December 2024: Invitations to authors
13 January 2025: Early bird (discounted) registration deadline
3 February 2025: Revised papers due
10 February 2025: Final registration deadline
25 March 2025: Rossfest Symposium (unrelated but possibly of interest)
26-27 March 2025: Security Protocols Workshop
For further details visit the web page at the top of this message. To be notified when the registration and paper submission pages open, , sign up on this Google form. Self-service unsubscribe at any time.








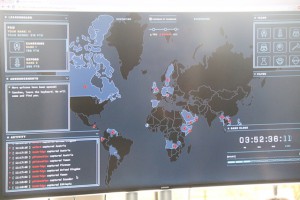
 The competition was played out on a “Risk-style” world map, and competing teams had to fight each other for control of several countries, each protected by a fiendish puzzle. A number of universities had also submitted guest challenges, and it was great that so many teams got involved in this creative process too. To give one example; The Cambridge team had designed a challenge based around a historically accurate enigma machine, with this challenge protecting the country of Panama. Competitors had to brute-force the settings of the enigma machine to decode a secret message. Other challenges were based around the core CTF subject areas of web application security, binary reverse engineering and exploitation, forensics, and crypto. Some novice teams may have struggled to compete, but they would have learned a lot, and hopefully developed an appetite for more competition. There were also plenty of teams present with advanced tool sets and a solid plan, with these preparations clearly paying off in the final scores.
The competition was played out on a “Risk-style” world map, and competing teams had to fight each other for control of several countries, each protected by a fiendish puzzle. A number of universities had also submitted guest challenges, and it was great that so many teams got involved in this creative process too. To give one example; The Cambridge team had designed a challenge based around a historically accurate enigma machine, with this challenge protecting the country of Panama. Competitors had to brute-force the settings of the enigma machine to decode a secret message. Other challenges were based around the core CTF subject areas of web application security, binary reverse engineering and exploitation, forensics, and crypto. Some novice teams may have struggled to compete, but they would have learned a lot, and hopefully developed an appetite for more competition. There were also plenty of teams present with advanced tool sets and a solid plan, with these preparations clearly paying off in the final scores.