I came across an unusual DHL branded phish recently…
The user receives an email with the Subject of “DHL delivery to [ xxx ]June ©2015” where xxx is their valid email address. The From is forged as “DHLexpress<noreply@delivery.net>” (the criminal will have used this domain since delivery.net hasn’t yet adopted DMARC whereas dhl.com has a p=reject policy which would have prevented this type of forgery altogether).
The email looks like this (I’ve blacked out the valid email address):
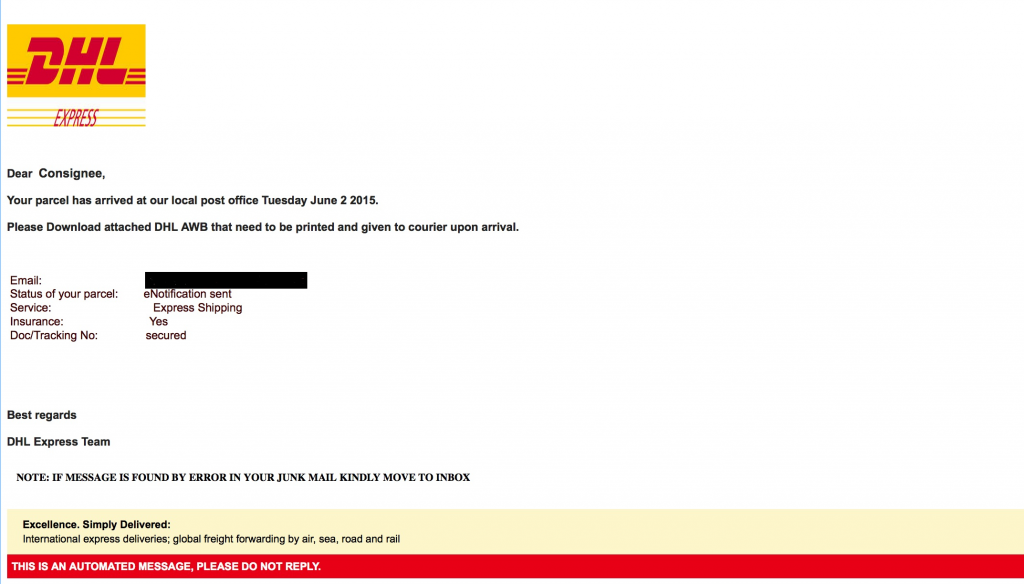
and so, although we would all wish otherwise, it is predictable that many recipients will have opened the attachment.
BTW: if the image looks in the least bit fuzzy in your browser then click on the image to see the full-size PNG file and appreciate how realistic the email looks.
I expect many now expect me to explain about some complex 0-day within the PDF that infects the machine with malware, because after all, that’s the main risk from opening unexpected attachments isn’t it ?
But no!
When opened, the PDF looks like this — and this time the image will look fuzzy in your browser and so will the full size version:
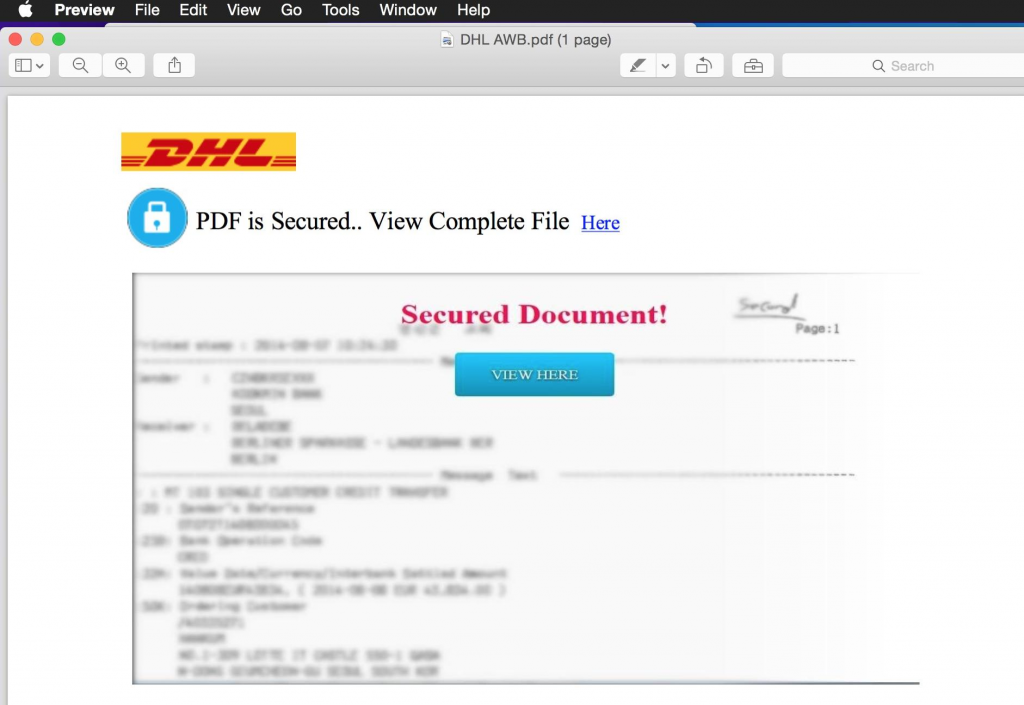
No, I did not do the blurring for privacy reasons, the criminal did the blurring in order to persuade the victim that they now had to click on the link (or button):
Once again, anyone expecting malware related activity at this point will be disappointed: the click then took you to a run-of-the-mill DHL impersonating website where the victim would have entered their credentials… in practice, these sites often collect email addresses and email passwords, so they’re often more of an attack on mail providers rather than DHL.
So why is the criminal using this complex method ?
The answer lies in the way that email filtering works. At present, the most that an email handling company will do with this email is to check that the PDF is well-formed and doesn’t contain known-malicious constructs (and the least is that it will be ignored altogether and passed through). So the presence of the URL will not be detected and the email will be delivered. Of course blacklisting the phishing site might cause the browser (or a toolbar) to throw up a warning to the user — but at a pretty late stage in the process when many will have pretty much made up their mind to view the “secure document” no matter what (recall my recent post about the high percentage of people who clicked through a Microsoft warning).
It should also be noted, in case there was any doubt as to whether the criminal really understands how modern email filtering works, that the email contains some advice about moving the email from the spam folder…. this will make no difference as to whether the attachment can be opened on any system I know of — but it will send a signal to the machine learning system that is dealing with incoming email. That signal is “oops you made an error” and as a result the criminal hopes that more of their email will be delivered to the inbox in the future.
> the email contains some advice about moving the email from the spam folder…. this will make no difference as to whether the attachment can be opened on any system I know of
Outlook (at least in some configurations) doesn’t allow attachments to be opened and doesn’t load external images for items that are in the spam folder. They must first be moved to the Inbox before potentially dangerous content will be loaded.
I just wish people could be taught to be even a little analytical when receiving this sort of email. The recipient of a delivery MUST have a valid email address AND be forced to go to the trouble of printing out something before a delivery from someone else can be made?